
Bath, Maine

And Other Bad Words

He was here just a minute ago…
When you’re angry at another driver, don’t flip them off – you’re just giving them something to back rage at. Give them a thumbs down instead.
You weren’t a dick, and the lingering sense of disapproval will haunt them all day.
Driving down I-93S tonight, in the vicinity of Wilmington, I caught lightning on the dashcam that lit up half the sky
I’m documenting something that wasn’t easy to uncover.
TL;DR – if you want to create a CNAME in Samba to replace an existing DNS record, you must delete the A record first.
I have an Active Directory domain running on Samba. I’ve had an underpowered file server, simply called ‘files’, for a while. I finally had a chance to upgrade it to some newer hardware with a rather large SSD.
Since this, like all my home projects, is a side-project that takes several days to complete I chose to build the new server (‘concord’) and get it running while leaving ‘files’ in-place.
I like to have servers named after their roles, because it makes things easy, but we have a lot more computers than formal roles in the house. We’ve finally settled on a naming convention: Windows names are places in Washington, Apple products are from California, and Linux products are from Massachusetts. (I am aware that Unix was birthed in New Jersey but… Ew. At least X came from MIT, that’s good enough for me.)
I also have a number of dependencies on the name ‘files’ including, most crucially, my own brain. Muscle memory is hard to overcome (“ls /net/files/… damn ^H/net/concord/…”) and I don’t want to relearn a server name.
That left me with three problems to solve: follow the naming standard, use a “taken” name for the server, and build said server while the needed name is still available on the network.
The obvious answer is to use CNAMEs. I planned to set up ‘files’ as an alias to ‘concord’. Similar practice would carry us forward through an indefinite number of role-swaps in the future.
After copying all of our data from ‘files’ to ‘concord’ I confidently shut ‘files’ down and added my CNAME. This is where things went wrong.
After shutting ‘files’ down, I started by creating the CNAME:
dc1 # samba-tool dns add 192.168.1.2 ad.jonesling.us files CNAME concord.ad.jonesling.us -U administrator Password for [AD\administrator]: ****** Record added successfully
That’s all well and good. Let’s test it out from another computer:
natick $ nslookup > files Server: dc1 Address: 2001:470:1f07:583:44a:52ff:fe4a:8cee#53 Name: files.ad.jonesling.us Address: 192.168.1.153 files.ad.jonesling.us canonical name = concord.ad.jonesling.us.
Crap. That’s the correct canonical name, but the wrong IP address – it’s ‘files’ old IP address.
Some googling uncovered someone with a similar issue back in 2012, but they “solved” it by creating static A records instead. That’s not a great solution, certainly not what I want.
I thought about it for a few minutes. I got a success message, but was the record actually created? How can I tell? What happens if I insert it again?
dc1 # samba-tool dns add 192.168.1.2 ad.jonesling.us files CNAME concord.ad.jonesling.us -U administrator
Password for [AD\administrator]: ******
ERROR(runtime): uncaught exception - (9711, 'WERR_DNS_ERROR_RECORD_ALREADY_EXISTS')
File "/usr/lib/python3.7/site-packages/samba/netcmd/__init__.py", line 186, in _run
return self.run(*args, **kwargs)
File "/usr/lib/python3.7/site-packages/samba/netcmd/dns.py", line 945, in run
raise e
File "/usr/lib/python3.7/site-packages/samba/netcmd/dns.py", line 941, in run
0, server, zone, name, add_rec_buf, None)Well, it was inserted somewhere, that much is clear.
What happens if I dig it? nslookup gave us a canonical address, but I want to see the actual DNS record. Maybe it contains a clue.
First, lets dig the CNAME:
dc1 # dig @dc1 files.ad.jonesling.us IN CNAME ; <<>> DiG 9.14.8 <<>> @dc1 files.ad.jonesling.us IN CNAME ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10370 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ; COOKIE: 7a0aa65a623d5d3bdbdc39075f2eff9d5b81dbd9ed05c9d0 (good) ;; QUESTION SECTION: ;files.ad.jonesling.us. IN CNAME ;; ANSWER SECTION: files.ad.jonesling.us. 900 IN CNAME concord.ad.jonesling.us. ;; Query time: 8 msec ;; SERVER: 192.168.1.2#53(192.168.1.2) ;; WHEN: Sat Aug 08 15:40:13 EDT 2020 ;; MSG SIZE rcvd: 100
I’ve bolded the line that shows the alias. That looks right.
But what about ‘files’?
dc1 # dig @dc1 files.ad.jonesling.us ; <<>> DiG 9.14.8 <<>> @dc1 files.ad.jonesling.us ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 42296 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ; COOKIE: 0352365b5c07ecdace1ebf3c5f2effa6da5d32bfe9002b32 (good) ;; QUESTION SECTION: ;files.ad.jonesling.us. IN A ;; ANSWER SECTION: files.ad.jonesling.us. 3600 IN A 192.168.1.153 ;; Query time: 8 msec ;; SERVER: 192.168.1.2#53(192.168.1.2) ;; WHEN: Sat Aug 08 15:40:22 EDT 2020 ;; MSG SIZE rcvd: 94
Ah. That looks like a conflict. Both records exist, and one has primacy over the other.
‘files’ was assigned an address via DHCP, I never gave it a static address, so I didn’t expect that I would need to delete anything. But if I think about it, I realized that Samba doesn’t know that ‘files’ isn’t coming back. (That makes me wonder what kind of graveyard DNS becomes, with friends’ phones and laptops popping in from time to time.)
So, can we delete the old A record, and what happens if we do?
We delete the address. It looks like it’s working:
dc1 # samba-tool dns delete 192.168.1.2 ad.jonesling.us files A 192.168.1.153 -U administrator Password for [AD\administrator]: Record deleted successfully
Was that the problem all along?
dc1 # dig @dc1 files.ad.jonesling.us ; <<>> DiG 9.14.8 <<>> @dc1 files.ad.jonesling.us ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38286 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ; COOKIE: 1610fb8ec07db8e3a43976ed5f2effdffeb142b30ca93848 (good) ;; QUESTION SECTION: ;files.ad.jonesling.us. IN A ;; ANSWER SECTION: files.ad.jonesling.us. 900 IN CNAME concord.ad.jonesling.us. concord.ad.jonesling.us. 3600 IN A 192.168.1.82 ;; Query time: 15 msec ;; SERVER: 192.168.1.2#53(192.168.1.2) ;; WHEN: Sat Aug 08 15:41:20 EDT 2020 ;; MSG SIZE rcvd: 116
That looks pretty good!
I met my robotic overlord, and I immediately pack-bonded to it.
Let me back up a little.
I am not a gardener. I hate taking care of lawns. I’m the type of person that likes to do a good job, do it well, get the result perfect – and then it should stay that way. I don’t like doing the same thing over and over. It gets dull, quickly.
A lawn takes a lot of work. It runs counter to my pleasure. No matter how well I do the job, in two weeks I have to do it all over again. So my lawn always looks like crap.
So this year I took my government-issued funny money (the CARES stimulus payment, AKA the COVID relief) and plowed it right back into economy. I bought an “automower.” Specifically, I purchased a Husqvarna 115H.
An automower is a Roomba for your lawn. You set a schedule and it takes care of getting the lawn trimmed and keeping itself charged. During operation it makes random passes over its mowing area and covers every square inch… eventually. It comes with a base station where it charges and “sleeps” when it’s not in use.
The mowing area is defined by a “boundary wire” that makes a continuous loop from the base station, around your yard, and back to the base station. (It is possible to have multiple mowing areas.). There is also a “guide wire” that extends from the base station to help the mower come home.
Automowers tend to be “mulching” mowers, meaning they leave their grass clippings in place instead of bagging them up and dumping them somewhere. Since they run so frequently this shouldn’t leave an unsightly mess; each cut should be millimeters in length. Mulching and leaving the grass clippings in place is better for the lawn, as well as making the mower simpler and far more reliable.
They’re convenient, but also environmentally conscious. They’re universally electric, making them quiet, emission-less, and built with a minimum of materials.
I purchased direct from Husqvarna. The mower arrived in just a couple of days. (Going through Lowes or Home Depot would have taken a week longer.) The box is an armload but can be managed by a single healthy adult.
Everything you need to set the mower up comes in the box, except housings to keep the power supply and base station dry. More on that in a moment.
The instructions were a bit unclear, but not terrible. There are steps that are in the quick setup guide that aren’t in the full guide, which is annoying, you need to read both.
There are diagrams, but they’re useless until you know what you’re doing – at which point you don’t need them anymore because the rules are quite logical.
The manual spends some time explaining complicated setups with multiple zones and islands, which may only apply to a minority of buyers, but no time spent on some of the most basic (and critical) steps: picking a spot for a base station and considerations for a guide wire.
From unboxing to the mower’s first run was about three hours of work.
Our yard is basically a square, less than two-tenths of an acre, and it’s all behind the house. We don’t have any complicated edges or ‘islands’ that require runs into the yard. Everything we need the mower to leave alone is in the outside edge.
We chose to lay the wire on the soil and stake it down, rather than trenching and burying it. The mower comes with plenty of stakes and wire; we used a fraction of one spool. If there were complicated sections we could easily have used more, but now we have enough leftover to fix mistakes and broken wires for a while.
Laying the wire on the soil was an easy choice because we have very little grass. Our yard was re-graded this spring and there’s still lots of bare soil. (We skipped hyro-seeding so we could customize the mix ourselves – wildflowers on the edge and lots of clover everywhere else.)
We stopped in the middle of set-up to run out and buy a 30 qt plastic tub, to make an ersatz garage for the base station. I’m not counting that time in the set-up time.
I may make a real “dog house” for it later.
Getting the mower itself running was very easy for me. I’m a technical person, your mileage may vary. You push it into the base station to start charging, set a security PIN to prevent theft, fill in some other information, and push “start.” That’s about it for the year, unless you want to make changes.
The unit is quiet. It’s much quieter than I expected. I expected moderate electric lawnmower noise, but I got nearly-silent operation. It’s “guaranteed” to be 59 decibels or less, but as a layman I have no point of reference for that. Suffice it to say, it’s super quiet.
It’s very fun to watch. I immediately started rooting for it to knock down tall sprigs of grass and other vegetation. It’s good to watch it to make sure you set the boundaries properly, leaving enough room for “overage.” It will cross the boundary a little, you can’t make tight margins.
We’ve had it running for less than 24 hours and it’s reached pretty much every point on the lawn.
If the mower crosses a boundary, hits something that activates the bump sensor, or gets confused, it backs up and tries a new direction. That seems to be a simple and effective solution.
Here’s a video of the mower in action this morning:
There is a stand of taller weeds emigrating from a neighbor’s yard, which took over that side of the yard last year. It has already re-sprouted and grown to a foot high since we re-graded the yard a few weeks ago. If we let it go all summer again, it will grow into two-meter-tall woody stalks. The mower has been slowly nibbling it back until the bump sensor activates, and has already cut down nearly all of it – about 2 square meters (6 square feet). We might have to weed the very edge of the fence, but that’s it.
Autonomous mowers might not be a good mower for some situations:
Despite some frustration with the setup instructions, the first 24 hours have gone swimmingly and I’m very happy. This might be the first time in my adult, home-owning life that I’ve had a neat lawn for more than a week per summer.
Having a real, autonomous, domestic robot makes the future feel like it’s finally arriving.
I think that, were I an A-list actor, I would ask for bit parts in Air Disasters.
I would take roles like a random passenger. Non-speaking, maybe three seconds of screen time at most, just something fun for me and for fans.
I’ve seen small time actors from other shows, such as Russell Ferrier (whom I recognized from an Outer Limits episode), which is a treat. But could you imagine spotting Robert DeNiro in the cabin, or Jessica Chastain in the background of a tower scene?
…it is needless for me to keep saying, I hope, except for emphasis, that each one of my children will rise to the full height of your possibilities, which means the possession of these eight cardinal virtues which constitutes a lady or gentleman.
1st. Be clean both inside and out.
2nd. Neither look up to the rich or down on the poor.
3rd. Lose, if need be, without squealing.
4th. Win without bragging.
5th. Always be considerate of women, children, and older people.
6th. Be too brave to lie.
7th. Be too generous to cheat.
8th. Take your share of the world and let others take theirs.
Source, page 24
This is the first in an occasional series of documents on WordPress.
WordPress is ubiquitous but fragile. There are few alternatives that provide the easy posting, wealth of plugins, and integration of themes, while also being (basically) free to use.
It’s also a nerve-wracking exercise in keeping bots and bad actors out. Some of the historical security holes are legendary. It doesn’t take long to find someone who experienced a site where the comments section was bombed by a spammer, or even outright defacement. (I will reluctantly raise my own hand, having experienced both in years past.)
Most people that use WordPress nowadays rely on 3rd parties to host it. This document isn’t for them; hosted security is mostly outside of your control. That’s generally a good thing: professionals are keeping you up to date and covered by best practices.
The rest of us muddle through security and updates in piece-meal fashion, occasionally stumbling over documents like this one.
As a rule, good server hygiene demands that you keep an eye on your logs. Tools like goaccess help you analyze usage, but nothing beats a peek at the raw logs for noticing issues cropping up.
Sleepy websites like mine show a high proportion of “good” bots like Googlebot, compared to human traffic. They’re doing good things like crawling (indexing) your site.
In my case they are the primary visitor base to my site, generating hundreds or even thousands of individual requests per day. Hopefully your own WordPress site has a better visitor-to-bot ratio than mine.
We don’t want to block these guys from their work, they’re actually helpful.
You’ll also see bad bots, possibly lots of them. Most are attempting to guess user credentials so they can post things on your WordPress site.
Some are fairly up-front about it:
... 132.232.47.138 [07:51:14] "POST /xmlrpc.php HTTP/1.1" 132.232.47.138 [07:51:14] "POST /xmlrpc.php HTTP/1.1" 132.232.47.138 [07:51:15] "POST /xmlrpc.php HTTP/1.1" 132.232.47.138 [07:51:16] "POST /xmlrpc.php HTTP/1.1" 132.232.47.138 [07:51:16] "POST /xmlrpc.php HTTP/1.1" 132.232.47.138 [07:51:18] "POST /xmlrpc.php HTTP/1.1" ...
They’ll hammer your server like that for hours.
Blocking their individual IP addresses at the firewall is devastatingly effective… for about five minutes. Another bot from another IP will pop up soon. Blocking individual IPs is a game of whack-a-mole.
Some are part of a “slow” botnet, hitting the same page from unique a IP address each time. These are part of the large botnets you read about.
83.149.124.238 [05:01:06] "GET /wp-login.php HTTP/1.1" 200 83.149.124.238 [05:01:06] "POST /wp-login.php HTTP/1.1" 200 188.163.45.140 [05:03:38] "GET /wp-login.php HTTP/1.1" 200 188.163.45.140 [05:03:39] "POST /wp-login.php HTTP/1.1" 200 90.150.96.222 [05:04:30] "GET /wp-login.php HTTP/1.1" 200 90.150.96.222 [05:04:32] "POST /wp-login.php HTTP/1.1" 200 178.89.251.56 [05:04:42] "GET /wp-login.php HTTP/1.1" 200 178.89.251.56 [05:04:43] "POST /wp-login.php HTTP/1.1" 200
These are more insidious: patient and hard to spot on a heavily-trafficked blog.
You (hopefully) installed WordPress to a location outside of your “htdocs” document tree. If not, you should fix that right away! (Consider this “security tip #0” because without this you’re basically screwed.)
Security tip #1 is to make sure auto updates are enabled. The slight risk of a botched release being automatically applied is much lower than that of having an critical security patch that is applied too late.
Like medieval door locks on your front door, there is little security advantage to running old software.
Once an exploit is patched, the prior releases are vulnerable as people deconstruct the patch and reverse-engineer the exploit(s) – assuming a exploit wasn’t published before the patch was released.
Your Apache configuration probably contains a section similar to this:
<Directory "/path/to/wordpress">
...
Require all granted
...
</Directory>We’re going to add some items between <Directory></Directory> tags to restrict access to the most vulnerable pieces.
We’ll start by invoking the Principle of Least Privilege: people should only be able to do the things they must do, and nothing more.
xmlrpc.php is an API for applications to talk to WordPress. Unfortunately it doesn’t carry extra security, so if you’re a bot it’s great to hammer with your password guesses – you won’t be blocked, and no one will be alerted.
Most people don’t need it. Unless you know you need it, you should disable it completely.
<Directory "/path/to/wordpress">
...
<Files xmlrpc.php>
<RequireAll>
Require all denied
</RequireAll>
</Files>
</Directory>There are WordPress plugins that purport to “disable” xmlrpc.php, but they deny access from within WordPress. That means that you’ve still paid a computational price for executing xmlrpc.php, which can be steeper than you expect, and you’re still at risk of exploitable bugs within it. Denying access to it at the server level is much safer.
This next change will block anyone from outside your LAN from logging in. That means that if you’re away from home you won’t be able to log in, either, without tunneling back home.
<Directory "/path/to/wordpress">
...
<Files wp-login.php>
<RequireAll>
Require all granted
# remember that X-Forwarded-For may contain multiple
# addresses, don't just search for ^192...
Require expr %{HTTP:X-Forwarded-For} =~ /\b192\.168\.1\./
</RequireAll>
</Files>
</Directory>If you’re not using a public-facing proxy, and don’t need to look at X-Forwarded-For, you can simplify this a little:
<Directory "/path/to/wordpress">
...
<Files wp-login.php>
<RequireAll>
Require all granted
Require ip 192.168.1
</RequireAll>
</Files>
</Directory>This will prevent 3rd parties from signing up on your blog and submitting comments. This may be important to you.
After inserting these blocks, you should execute Apache’s ‘configtest’ followed by reload:
$ sudo apache2ctl configtest apache2 | * Checking apache2 configuration ... [ ok ]
$ sudo apache2ctl reload apache2 | * Gracefully restarting apache2 ... [ ok ]
Now test your changes from outside your network:
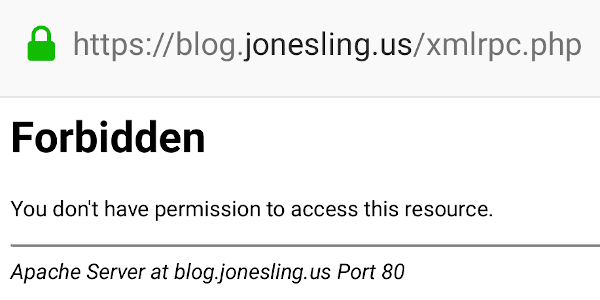
Apache’s access log should show a ‘403’ (Forbidden) status:
... "GET /xmlrpc.php HTTP/1.1" 403 ...
And just like that, you’ve made your WordPress blog a lot more secure.
Interestingly, by making just these changes on my own site the attacks immediately dropped off by 90%. I guess that the better-written bots realized that I’m not a good target anymore and stopped wasting their time, preferring lower-hanging fruit.
A quick note about the blog’s new name.
While re-watching The Abominable Bride with a clogged ear, I mis-heard a reference to the Obliquity of the Ecliptic. The resulting phrase, “The Ubiquity of the Ecliptic,” was confusingly vague and mysterious, just like “A Random Flamingo” was. Perfect for a family journal.