My ISP is pretty terrible but living in the United States, as I do, effectively makes internet service a regional monopoly. In my case, not only do I pay too much for service but certain websites (cough google.com cough) are incredibly slow for no reason other than my ISP is a dick and won’t peer with them properly.
This particular ISP, despite being very large, has so far refused to roll out IPv6. This was annoying until I figured out that I could use this to my advantage. If they won’t peer properly over IPv4, maybe I can go through a tunnel broker to get IPv6 and route around them. Surprisingly, it worked beautifully. GMail has never loaded so fast at home.
It was beautiful, that is, until I discovered an unintended side effect: Netflix stopped working.
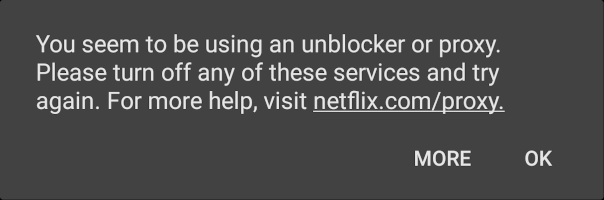
A quick Google search confirmed my suspicion. Netflix denies access to known proxies, VPNs, and, sadly, IPv6 tunnel brokers. My brave new world was about to somewhat less entertaining if I couldn’t fix this.
Background
Normally a DNS lookup returns both A (IPv4) and AAAA (IPv6) records together:
$ nslookup google.com Server: 192.168.1.2 Address: 192.168.1.2#53 Non-authoritative answer: Name: google.com Address: 172.217.12.142 Name: google.com Address: 2607:f8b0:4006:819::200e
Some services will choose to provide multiple addresses for redundancy; if the first address doesn’t answer then your computer will automatically try the next in line.
Netflix in particular will return a large number of addresses:
$ nslookup netflix.com 8.8.8.8 Server: 8.8.8.8 Address: 8.8.8.8#53 Non-authoritative answer: Name: netflix.com Address: 54.152.239.3 Name: netflix.com Address: 52.206.122.138 Name: netflix.com Address: 35.168.183.177 Name: netflix.com Address: 54.210.113.65 Name: netflix.com Address: 52.54.154.226 Name: netflix.com Address: 54.164.254.216 Name: netflix.com Address: 54.165.157.123 Name: netflix.com Address: 107.23.222.64 Name: netflix.com Address: 2406:da00:ff00::3436:9ae2 Name: netflix.com Address: 2406:da00:ff00::6b17:de40 Name: netflix.com Address: 2406:da00:ff00::34ce:7a8a Name: netflix.com Address: 2406:da00:ff00::36a5:f668 Name: netflix.com Address: 2406:da00:ff00::36a5:9d7b Name: netflix.com Address: 2406:da00:ff00::23a8:b7b1 Name: netflix.com Address: 2406:da00:ff00::36d2:7141 Name: netflix.com Address: 2406:da00:ff00::36a4:fed8
The Solution
The key is to have your local DNS resolver return A records, but not AAAA, if (and only if) it’s one of Netflix’s hostnames.
Before I document the solution, it helps to know my particular setup and assumptions:
- IPv6 via a tunnel broker
- BIND’s named v9.14.8
Earlier versions of BIND are configured somewhat differently: you may have different options, or (if it’s a really old build) you may need to run two separate named instances. YMMV.
Step 0: Break Out Your Zone Info (optional but recommended)
If your zone info is part of named.conf you really should put it into it’s own file for easier maintenance and re-usability. The remaining instructions won’t work, without modification, if you don’t.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | # /etc/bind/local.confzone "." in { type hint; file "/var/bind/named.cache";};zone "localhost" IN { type master; file "pri/localhost.zone"; notify no;};# 127.0.0. zone.zone "0.0.127.in-addr.arpa" { type master; file "pri/0.0.127.zone";}; |
Step 1: Add a New IP Address
You can run a single instance of named but you’ll need at least two IP addresses to handle responses.
In this example the DNS server’s “main” IP address is 192.168.1.2 and the new IP address will be 192.168.1.3.
How you do this depends on your distribution. If you’re using openrc and netifrc then you only need to modify /etc/conf.d/net:
1 2 | # Gentoo and other netifrc-using distributionsconfig_eth0="192.168.1.2/24 192.168.1.3/24" |
Step 2: Listen To Your New Address
Add your new IP address to your listen-on directive, which is probably in /etc/bind/named.conf:
1 | listen-on port 53 { 127.0.0.1; 192.168.1.2; 192.168.1.3; }; |
It’s possible that your directive doesn’t specify the IP address(es) and/or you don’t even have a listen-on directive – and that’s ok. From the manual:
The server will listen on all interfaces allowed by the address match list. If a port is not specified, port 53 will be used… If no listen-on is specified, the server will listen on port 53 on all IPv4 interfaces.
https://downloads.isc.org/isc/bind9/9.14.8/doc/arm/Bv9ARM.ch05.html
Everything I just said also applies to listen-on-v6.
Step 3: Filter Query Responses
Create a new file called /etc/bind/limited-ipv6.conf and add the following at the top:
1 2 3 4 5 6 7 8 | view "internal-ipv4only" { match-destinations { 192.168.1.3; }; plugin query "filter-aaaa.so" { # don't return ipv6 addresses filter-aaaa-on-v4 yes; filter-aaaa-on-v6 yes; };}; |
What this block is saying is, if a request comes in on the new address, pass it through the filter-aaaa plugin.
We’re configuring the plugin to filter all AAAA record replies to ipv4 clients (filter-aaaa-on-v4) and ipv6 clients (filter-aaaa-on-v6).
Now add a new block after the first block, or modify your existing default view:
1 2 3 4 5 6 7 8 9 10 11 | # forward certain domains back to the ipv4-only viewview "internal" { include "/etc/bind/local.conf"; # AAAA zones to ignore zone "netflix.com" { type forward; forward only; forwarders { 192.168.1.3; }; };}; |
This is the default view for internal clients. Requests that don’t match preceding views fall through here.
We’re importing the local zone from step 0 (so we don’t have to maintain two copies of the same information), then forwarding all netflix.com look-ups to the new IP address, which will be handled by the internal-ipv4only view.
Step 4: Include the New Configuration File
Modify /etc/bind/named.conf again, so we’re loading the new configuration file (which includes local.conf).
1 2 | #include "/etc/bind/local.conf";include "/etc/bind/limited-ipv6.conf"; |
Restart named after you make this change.
Testing
nslookup can help you test and troubleshoot.
In the example below we call the “normal” service and get both A and AAAA records, but when we call the ipv4-only service we only get A records:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | $ nslookup google.com 192.168.1.2Server: 192.168.1.2Address: 192.168.1.2#53Non-authoritative answer:Name: google.comAddress: 172.217.3.110Name: google.comAddress: 2607:f8b0:4006:803::200e$ nslookup google.com 192.168.1.3Server: 192.168.1.3Address: 192.168.1.3#53Non-authoritative answer:Name: google.comAddress: 172.217.3.110 |